Before we get started, have you tried our new Python Code Assistant? It's like having an expert coder at your fingertips. Check it out!
In this tutorial, we'll explore the exciting world of Bluetooth device discovery using Python. Our focus will be on writing a script that scans for nearby Bluetooth devices and retrieves valuable information about them. This skill is not only valuable for understanding Bluetooth technology but also has practical applications in cybersecurity and ethical hacking.
Bluetooth, being a widely used wireless communication protocol, presents both opportunities and challenges for security enthusiasts. By learning how to scan and gather information about nearby devices programmatically, you'll be equipped with a fundamental skill set that can be applied to various scenarios, from identifying potential security risks to conducting ethical hacking assessments.
The Significance in Cybersecurity and Ethical Hacking
Understanding Bluetooth device discovery is a crucial aspect of networking, ethical hacking, and cybersecurity in general. This script serves as a foundation for exploring the security implications of Bluetooth technology.
Ethical hackers often use similar techniques to identify vulnerable devices, assess security postures, and conduct penetration testing. By scanning for active Bluetooth devices and obtaining details such as device names, classes, and even MAC (Media Access Control) addresses, security professionals can identify potential targets for further analysis.
Additionally, this knowledge is essential for recognizing and addressing security risks associated with Bluetooth, such as unauthorized device connections and vulnerabilities that malicious actors may exploit.
By learning to scan Bluetooth devices, hackers could perform malicious activities like device impersonation, man-in-the-middle attacks, and Bluetooth profile weaknesses. This knowledge may lead to unauthorized access, data interception, or even denial-of-service attacks if proper security measures are not in place.
Let’s see how to implement this in Python. We’ll be making use of the PyBluez module. PyBluez is a Python module that provides Bluetooth functionality, allowing developers to implement Bluetooth communication and control Bluetooth-enabled devices. We’ll also be writing this program in Python 3.
Install PyBluez by running the following command on your cmd/Terminal:
$ pip install pybluez2One very important thing to note is that the success of running the provided code may vary on virtual machines due to differences in Bluetooth compatibility. For a more reliable assessment, it is recommended to test the code on a physical machine with native Bluetooth support.
Now, let’s get to the code. Open up a Python file, name it meaningfully (like bluetooth_scanner.py) and follow along:
# Import bluetooth from the PyBluez module.
import bluetooth
def scan_bluetooth_devices():
try:
# Discover Bluetooth devices with names and classes.
discovered_devices = bluetooth.discover_devices(lookup_names=True, lookup_class=True)
# Display information about the scanning process.
print('[!] Scanning for active devices...')
print(f"[!] Found {len(discovered_devices)} Devices\n")
# Iterate through discovered devices and print their details.
for addr, name, device_class in discovered_devices:
print(f'[+] Name: {name}')
print(f'[+] Address: {addr}')
print(f'[+] Device Class: {device_class}\n')
except Exception as e:
# Handle and display any exceptions that occur during device discovery
print(f"[ERROR] An error occurred: {e}")
# Call the Bluetooth device scanning function when the script is run
scan_bluetooth_devices()This Python script utilizes the bluetooth module to scan for nearby Bluetooth devices and retrieve information about them.
The scan_bluetooth_devices() function attempts to discover Bluetooth devices by using the discover_devices() function from the bluetooth module with the parameters lookup_names=True and lookup_class=True to retrieve both device names and classes.
The script then prints a message indicating the start of the scanning process and the number of devices found. It iterates through the list of discovered devices, extracting and displaying details such as the device name, address, and device class. Any exceptions that might occur during the device discovery process are caught and handled, with an error message printed to inform the user. Finally, the function is called to execute the Bluetooth device scanning when the script is run.
Our result:
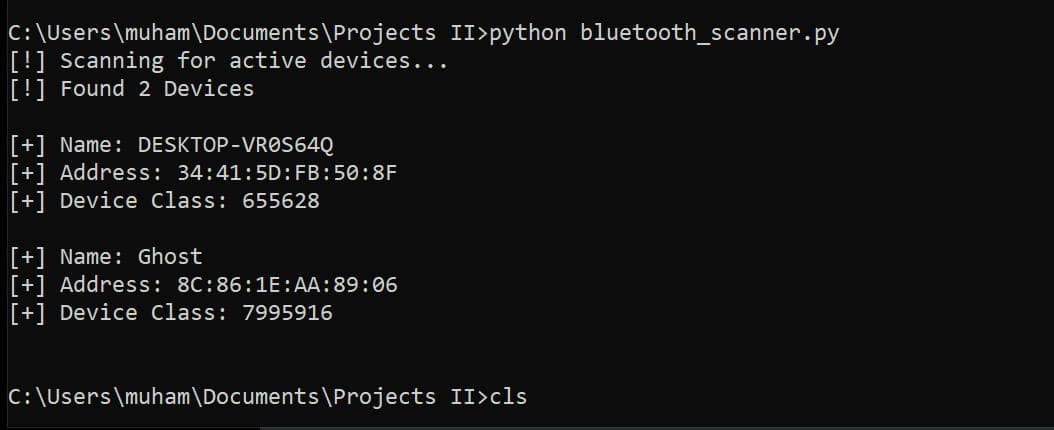
The result shows us the available Bluetooth devices around us, including their names, MAC Addresses, and Device classes.
Related: How to Make a MAC Address Changer in Python.
By obtaining MAC addresses from Bluetooth device discovery results, hackers can potentially manipulate or spoof their device's MAC address to impersonate legitimate devices. This could lead to unauthorized access, data interception, and security breaches, highlighting the importance of implementing strong security measures to prevent MAC address spoofing.
From our result, the Bluetooth device class 7995916 can be interpreted as follows:
- Binary Representation: The binary representation of
7995916is 11110100101101100101100
Now, breaking down this binary sequence into the major, minor, and service classes:
- Service Class (bits 0-1): The last two bits of the binary representation are 00, indicating that the service class is 0 in decimal.
- Minor Device Class (bits 2-7): The next six bits are 101100, which is 44 in decimal.
- Major Device Class (bits 8-12): The next five bits are 10100, which is 20 in decimal.
So, the interpretation of the device class 7995916 is as follows:
- Major Device Class: 20
- Minor Device Class: 44
- Service Class: 0
These numeric values can then be interpreted using the Bluetooth specifications. Referring to the Bluetooth Core Specification:
Device 1 (Major Device Class: 20, Minor Device Class: 44, Service Class: 0):
- Major Device Class (20): Computer
- Minor Device Class (44): Desktop Workstation
- Service Class (0): No specific service class
Therefore, DESKTOP-VR0S64Q is a computer, specifically a desktop workstation.
Device 2 (Major Device Class: 26, Minor Device Class: 4, Service Class: 0):
- Major Device Class (26): Phone
- Minor Device Class (4): Smartphone
- Service Class (0): No specific service class
Therefore, Ghost is a smartphone.
Both deductions are actually correct. These interpretations are based on the Bluetooth Core Specification documents provided by the Bluetooth Special Interest Group. Feel free to check it out here. Even if hackers don’t fully understand the class concept, with the device name and MAC address, they can still do much damage.
Learn also: How to Build a WiFi Scanner in Python using Scapy.
I hope you enjoyed this tutorial. Happy coding!
Found the article interesting? You'll love our Python Code Generator! Give AI a chance to do the heavy lifting for you. Check it out!
View Full Code Improve My Code

Got a coding query or need some guidance before you comment? Check out this Python Code Assistant for expert advice and handy tips. It's like having a coding tutor right in your fingertips!