Matched Python Tutorials and Topics

Keyboard module: Controlling your Keyboard in Python
Learn how to use keyboard module in Python to take full control of your keyboard such as hooking global events, registering hotkeys, simulating key presses and releases and much more.

How to Make a Keylogger in Python
Creating and implementing a keylogger from scratch that records key strokes from keyboard and send them to email or save them as log files using Python and keyboard library.

3 Best Online AI Code Generators
Explore the top 3 AI code generators—CodeConvert, ZZZ Code AI, and CodingFleet. Compare their features, pros, and cons to find the best tool for your coding needs, with CodingFleet leading for its advanced features and versatility.
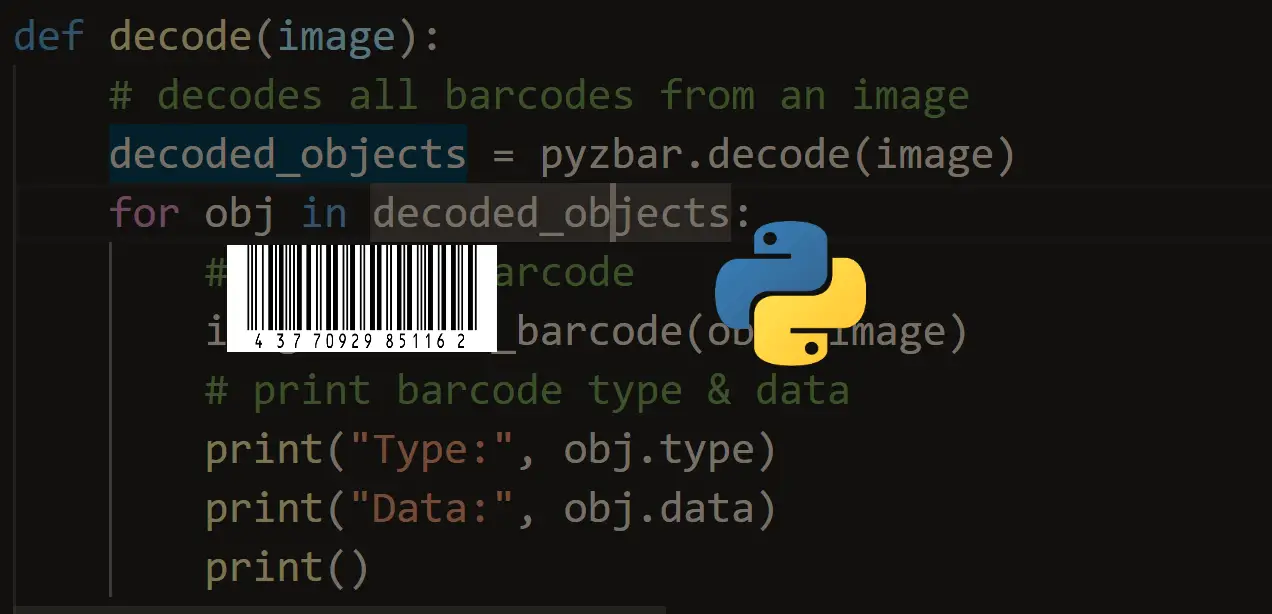
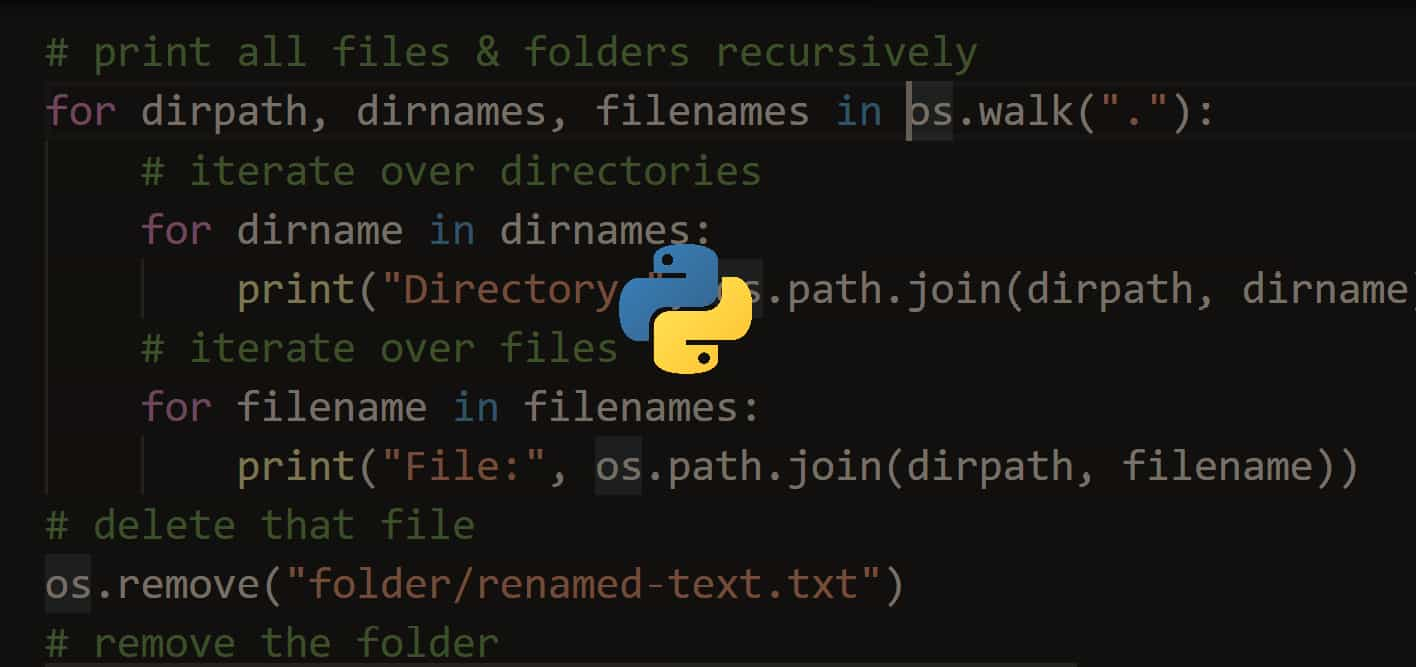
How to Make a Barcode Reader in Python
Learn how to make a barcode scanner that decodes barcodes and draw them in the image using pyzbar and OpenCV libraries in Python

How to Make a Bluetooth Device Scanner in Python
Master Bluetooth device scanning with Python: A concise tutorial on using PyBluez for discovering and analyzing nearby Bluetooth devices, essential for cybersecurity and ethical hacking.
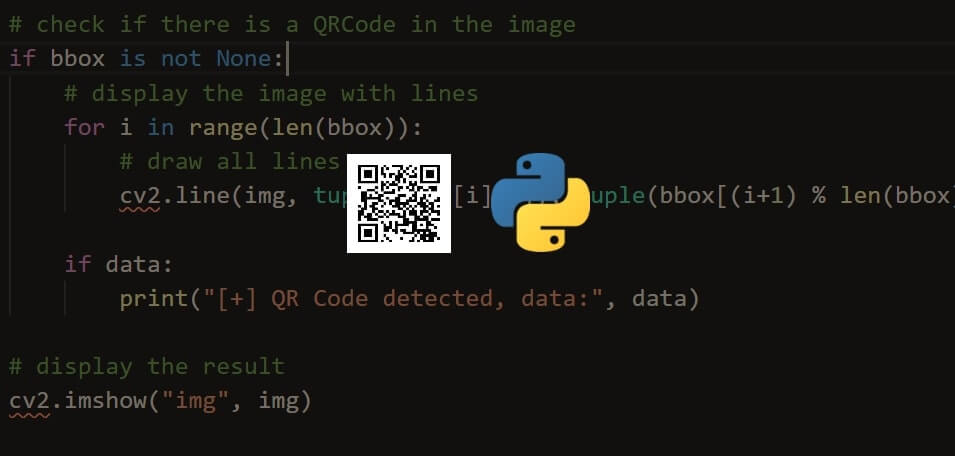
How to Generate and Read QR Code in Python
Learning how you can generate and read QR Code in Python using qrcode and OpenCV libraries.
Building an AI-Driven HTTP Security Headers Analyzer with Python
Build a Python tool that checks HTTP security headers and uses DeepSeek AI to provide practical insights, missing protections, and security recommendations.
Why Python Is Used for Cybersecurity
This article delves into the importance of cybersecurity for online businesses and why Python is a go-to programming language for cybersecurity experts. It highlights Python's various benefits, such as its simplicity, extensive libraries, and versatility across platforms. The article also discusses Python's limitations
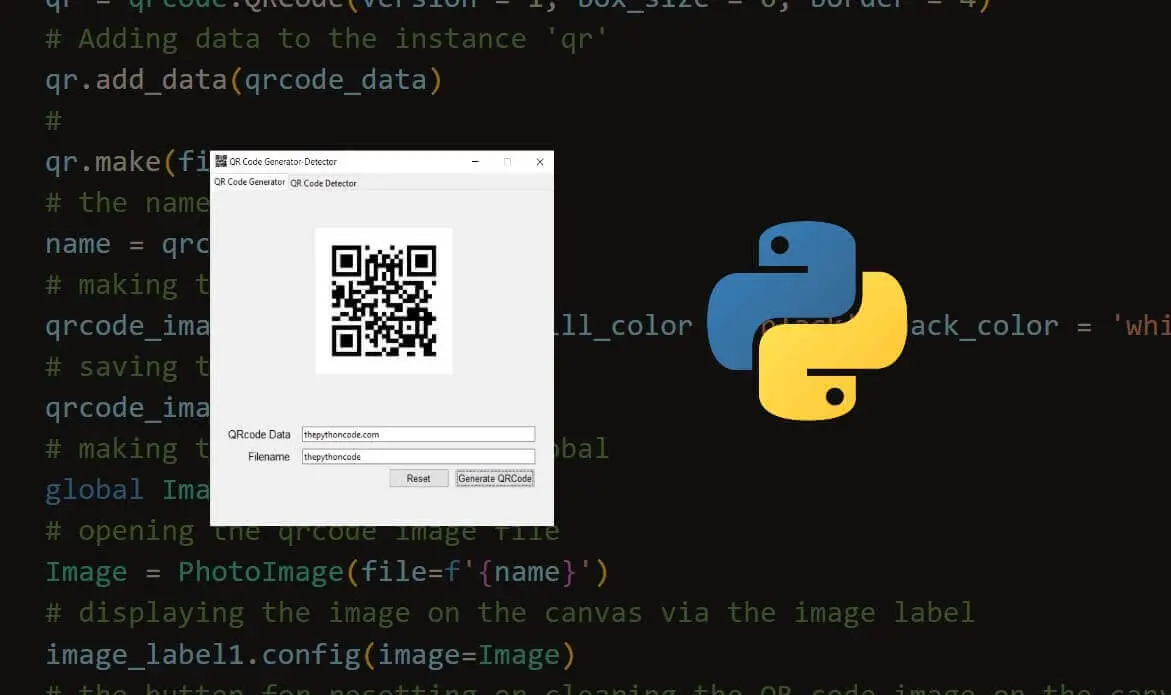
How to Build a GUI QR Code Generator and Reader in Python
Learn how to build a complete GUI QR code generator and reader program in Python using Tkinter, qrcode and OpenCV libraries.
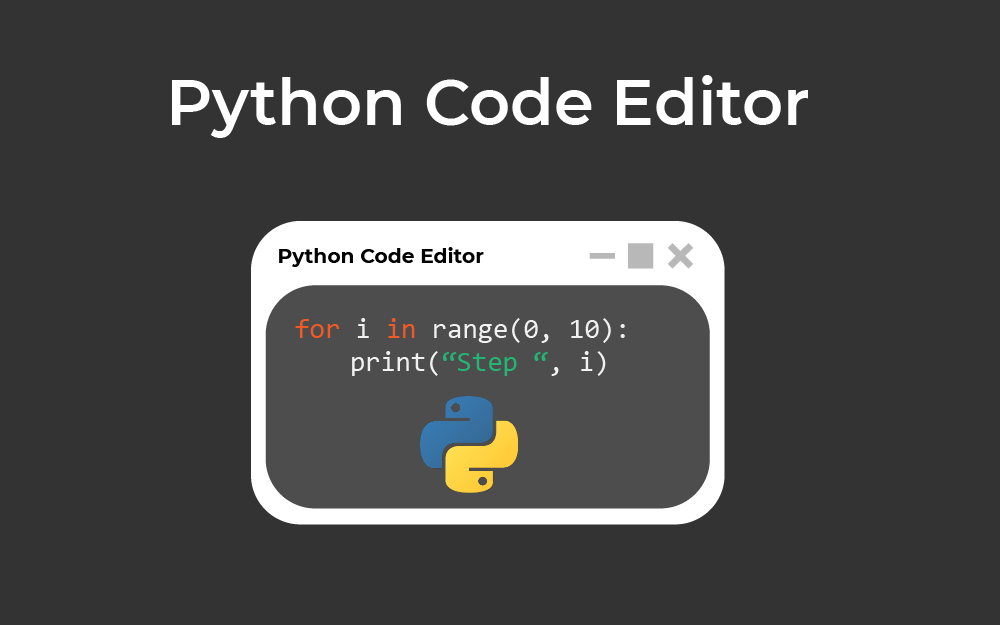
How to Make a Python Code Editor using Tkinter in Python
Learn how to make a simple python code editor that supports running the code and simple syntax highlighting using Tkinter in Python.
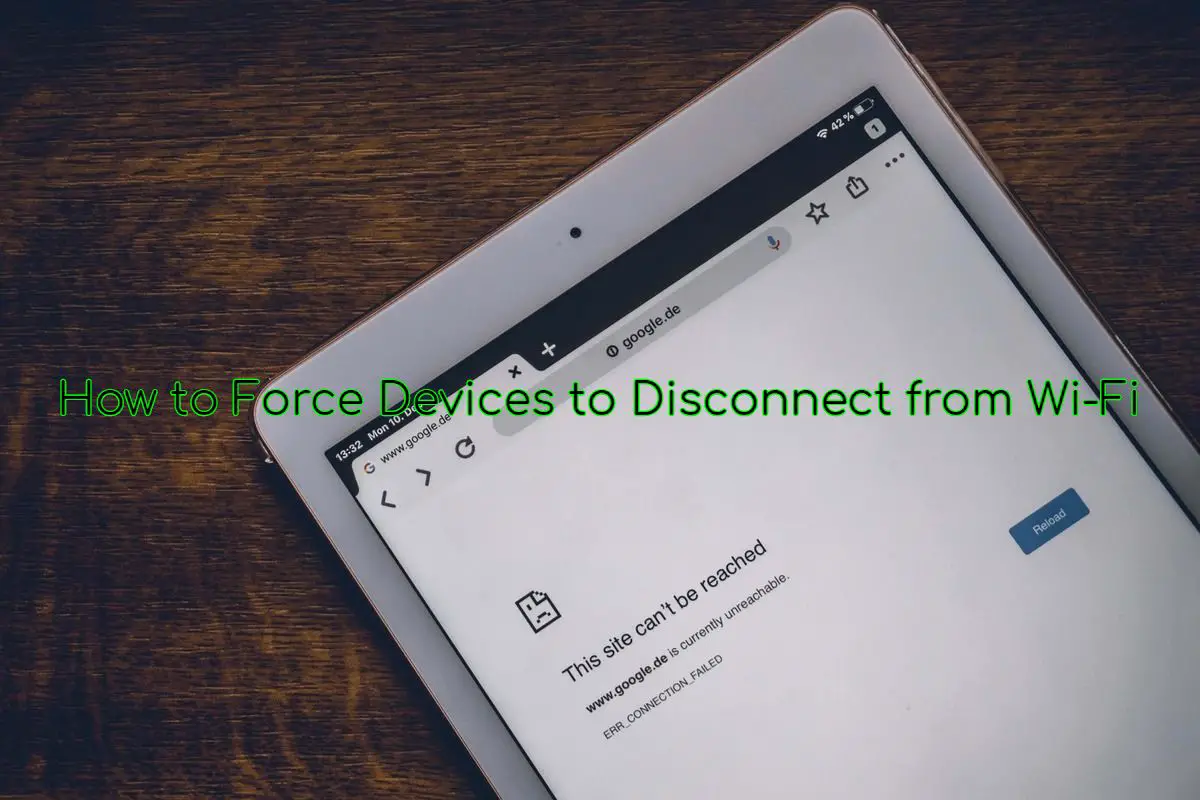
How to Disconnect Devices from Wi-Fi using Scapy in Python
Forcing devices to disconnect from a network by sending deauthentication frames continuously using Scapy library in Python, this is called deauthentication attack.

How to Implement the Vigenère Cipher in Python
Step-by-step guide to implementing the Vigenère Cipher in Python. Understand its mechanism, strengths, and vulnerabilities, with practical examples for encryption and decryption.
How to Add a TLS/SSL Certificate in Python Code
Learn how to secure your Python applications with TLS/SSL certificates. Understand the importance of these cryptographic protocols, and grasp how to integrate SSL certificates into Python code using requests library.
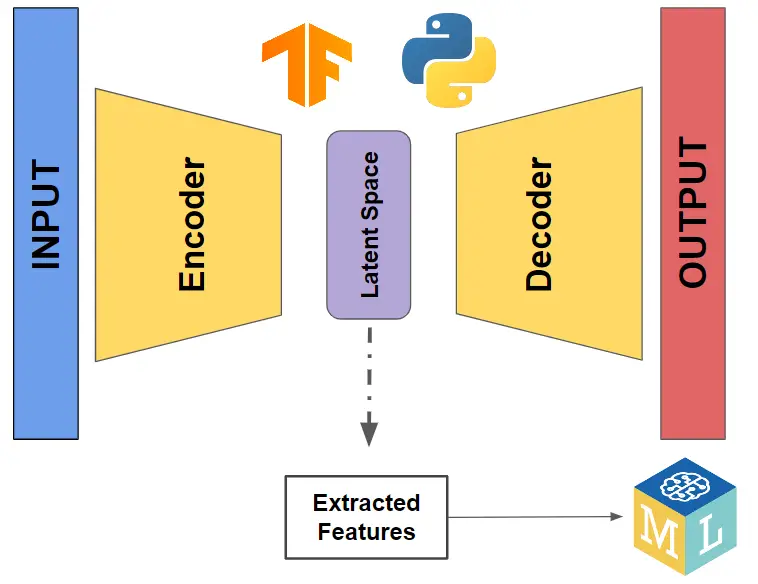
Autoencoders for Dimensionality Reduction using TensorFlow in Python
Learn how to benefit from the encoding/decoding process of an autoencoder to extract features and also apply dimensionality reduction using Python and Keras all that by exploring the hidden values of the latent space.

How to Lock PDFs in Python
Discover how to utilize the PyPDF2 library to password-protect and encrypt PDF files, ensuring top-notch security for sensitive documents. Learn to create a secure PDF locker and adopt strong password practices for enhanced cybersecurity.

A Comprehensive Guide to Non-Intrusive Vulnerability Testing
The article provides an overview of the process of non-intrusive vulnerability assessment, which is a security measure used to identify and fix security flaws in networks, data, and applications. It explains the three types of vulnerabilities that need to be addressed during the process: software, network, and configur
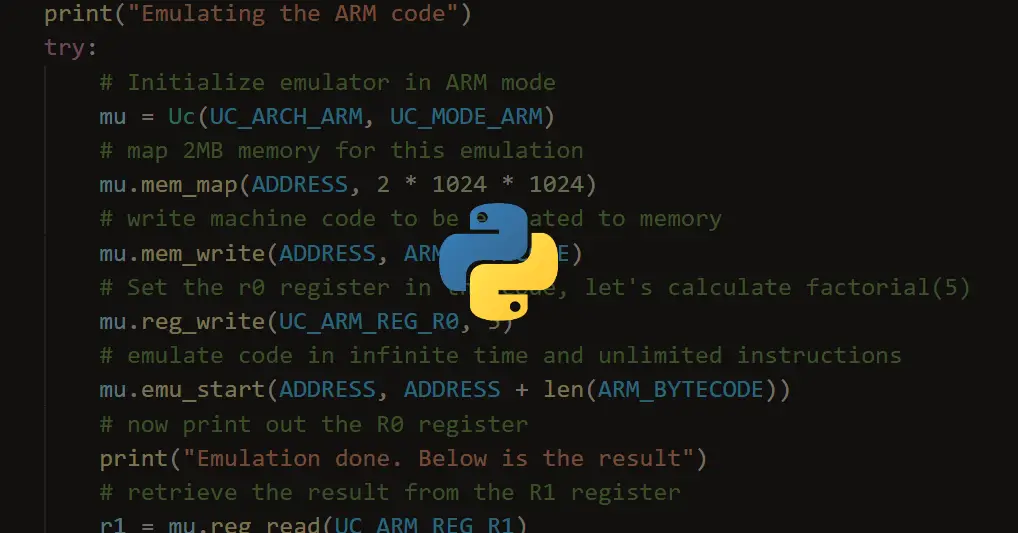
Assembly, Disassembly and Emulation using Python
Learn how to use Keystone engine, Capstone engine and Unicorn engine to assemble, disassemble and emulate machine code (ARM, x86-64 and more) in Python

How to Build a Password Manager in Python
Learn how to build a secure custom password manager using Python. This tutorial walks you through encryption, data storage, and various functionalities like adding, retrieving, and managing passwords. Elevate your online security game with some hands-on coding.

Python for Cyber Security: A Beginners Guide
A guide to Cybersecurity beginners and enthusiasts who want to learn the Python programming language.
How to Build a Custom Netcat with Python
Learn how to create a custom Python-based Netcat tool for network debugging, file transfers, and remote command execution. Perfect for networking and cybersecurity enthusiasts, this guide provides hands-on code and practical examples.
How to Create a Pong Game in Python
Discover how to craft a Pong game with Python and Pygame through a comprehensive tutorial, gaining hands-on game development skills. Learn key concepts like rendering graphics, managing game state, and handling user input while bringing your code to life in this engaging guide.

How to View Hidden Wi-Fi Networks in Python
Discover how to uncover hidden Wi-Fi networks using Python and Scapy. This tutorial debunks the security myth of hidden SSIDs and guides you through setting up your adapter in monitor mode to detect and log hidden networks, emphasizing practical network analysis and security assessment.

How to Crack the Affine Cipher in Python
Learn to crack the Affine Cipher in Python with this step-by-step guide. Explore classical cryptography, understand modular arithmetic and linear algebra in encryption, and master brute force decryption with practical Python code.

Automate Reports with Python
Learn how to automate report generation with Python in this article. Explore the process from environment setup to data preparation, report creation, customization, error handling, and security. Discover Python's versatility and efficiency in transforming the traditional way of preparing reports, saving time, and enhan

How to Perform IP Address Spoofing in Python
Master IP spoofing with Python: Dive into crafting fake IP addresses to test network security. Utilize Scapy and Faker in a hands-on tutorial to send spoofed ICMP packets, complete with practical examples and step-by-step instructions.

How to Build a Twitter (X) Bot in Python
Discover how to create a Twitter bot using Python and Tweepy in this concise guide. Learn to automate tweets with a simple bot that shares dog facts hourly, and delve into setting up a Twitter Developer account, handling API keys, and using OAuth for authentication.

How to Make a Login Password Guesser in Python
Master the art of ethical hacking with this hands-on tutorial on creating a Python-based login password guesser using brute-force techniques. Designed for educational purposes, this guide will level up your cybersecurity expertise.

How to Crack the Caesar Cipher in Python
Unlock the secrets of the Caesar cipher with our Python tutorial. Learn the ins and outs of one of history's oldest codes and how to break it using modern computing power.

How to Create a Zip File Locker in Python
Discover how to protect your ZIP files with a custom Python script in this tutorial. Learn to enforce strong passwords using pyzipper and safeguard your data from cyber threats. Perfect for programmers who love to DIY their security tools!

How to Implement the Caesar Cipher in Python
Learn to code the Caesar cipher in Python and encrypt messages like Julius Caesar! This beginner-friendly tutorial covers the basics of one of history's earliest ciphers with step-by-step coding instructions. Dive into the world of ancient cryptography!

How to Control your Mouse in Python
Controlling computer mouse in python. Hooking events, registering hotkeys, simulating mouse movements and click, and much more.

Nearshore vs Offshore: Cost-Effective Software Development
Discover the key differences between nearshore and offshore software development. Learn which model offers the best balance of cost, quality, and collaboration for your project.

Unveiling the Power of Python in Network Engineering and Automation
This article delves into how Python empowers network engineering with easy automation, efficient monitoring, enhanced security, rapid prototyping, and seamless troubleshooting, making it a cost-effective and transformative tool in the industry.
How to Get Google Page Ranking in Python
Learn how to use Google Custom Search Engine API to get the keyword position ranking of a specific page in Python.

How to Create Videos from Images in Python
Learn how to create videos from image arrays using Python and OpenCV, focusing on timelapses. Setting up OpenCV, using argparse for input parameters, and processing images in batches. Key steps include configuring the VideoWriter object, iterating over images to build the video, and tips for efficient memory use.

How to Implement 2FA in Python
Learn how to enhance security with Python by implementing Two-Factor Authentication (2FA) using TOTP and HOTP algorithms. This comprehensive guide covers everything from generating OTPs with pyotp to integrating with authenticator apps.
How to Get Geolocation in Python
Learn how to use GeoPy library to geocode physical addresses into latitude and longitude and vice versa; getting latitude and longitude from addresses, towns, cities and more in Python.

How to Remove Metadata from Images in Python
Learn to protect your privacy by deleting metadata from images using Python and the Pillow library in this step-by-step tutorial, perfect for enhancing security.

How to Cartoonify Images in Python
Learn how to cartoonify images using Python and OpenCV in this step-by-step tutorial. Transform regular photos into cartoon-like visuals with just a few lines of code. Perfect for beginners in computer vision.
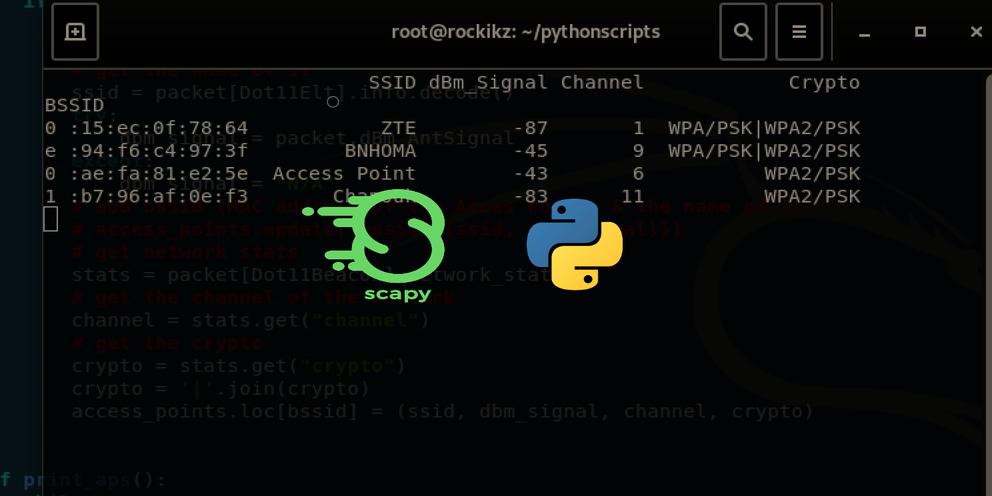
How to Build a WiFi Scanner in Python using Scapy
Building a Wi-Fi scanner in Python using Scapy that finds and displays available nearby wireless networks and their MAC address, dBm signal, channel and encryption type.

How to Perform Reverse DNS Lookups Using Python
Learn how to perform reverse DNS lookups and find other websites hosted on the same server using Python and the ViewDNS API. Perfect for network administrators and cybersecurity professionals.
How to Extract Text from PDF in Python
Learn how to extract text as paragraphs line by line from PDF documents with the help of PyMuPDF library in Python.
How to Use Shodan API in Python
Learn how to use Shodan API to make a script that searches for public vulnerable servers, IoT devices, power plants and much more using Python.
How to Encrypt and Decrypt Files in Python
Encrypting and decrypting files in Python using symmetric encryption scheme with cryptography library.
How to Create a RESTful API with Flask in Python
Learn to build a RESTful API using Flask, Python, and SQLite, covering setup, CRUD operations, database integration, and best practices for code organization.
How to Inject Code into HTTP Responses in the Network in Python
Learn how you can inject Javascript, HTML or CSS to HTTP response packets in a spoofed network using Scapy and NetfilterQueue in Python.

How to Create Fake Access Points using Scapy in Python
Creating fake access points and fooling nearby devices by sending valid beacon frames to the air using scapy in python.

How to Make a Facial Recognition System in Python
Master Python facial recognition with our step-by-step tutorial. Build real-time and image upload systems to identify faces with precision. Essential for security, attendance, and more. Perfect for beginners. Dive into the biometric tech world now!
How to Make a Ransomware in Python
Learn how to build a ransomware using symmetric encryption (AES algorithm) with the help of cryptography library in Python.
How to Build a GUI Voice Recorder App in Python
Learn how to build a voice recorder GUI app using Tkinter and sounddevice libraries in Python.
Tokenization, Stemming, and Lemmatization in Python
This article discusses the preprocessing steps of tokenization, stemming, and lemmatization in natural language processing. It explains the importance of formatting raw text data and provides examples of code in Python for each procedure.

How to Remove Metadata from PDFs in Python
Learn to safeguard privacy by removing metadata from PDFs using Python's PyPDF2 in this tutorial. Discover how metadata can expose sensitive information and how to erase it to protect confidentiality, with step-by-step code guidance and practical examples.
How to Extract YouTube Data using YouTube API in Python
Learn how to extract YouTube data including video and channel details, searching by keyword or channel and extracting comments with YouTube API in Python.
